V-ID

INTRODUCTION
All cryptocurrencies enthusiast know what is a Trezor, Nano Ledger and many more. For those who dont know what hardware wallet, hardware wallet is a special type of bitcoin and another platforms wallet which stores the user's private keys in a secure hardware device. They have major advantages over standard software wallets such as :
private keys are often stored in a protected area of a microcontroller, and cannot be transferred out of the device in plaintext
immune to computer viruses that steal from software wallets
can be used securely and interactively, private keys never need to touch potentially vulnerable software
much of the time, the software is open source, allowing a user to validate the entire operation of the device.
PRESENTATION
V-ID is the best contender to end up a true standard answer for record misrepresentation.
The administration utilizes normal and solid standards to confirm and check any advanced document of any distributor. This is conceivable because of the perpetual and straightforward nature of the barricade.
Among the main clients who as of now utilize V-ID, are Airbus Defense Space, ESHRE European Research Institute and Vitrumnet optical fiber provider.
The issuing association can enroll any document through the V-ID check process, enabling every beneficiary to confirm its credibility in short order and for nothing out of pocket. V-ID does not spare a duplicate of the checked record and hence effortlessly consents to the proposals of the GDPR.
The Utility V-ID current offers a particular included an incentive for distinguishing issuing associations, putting away advanced fingerprints in a scholarly contract, and preparing installments for confirmation.
Theme
At the point when the network proceeds with the digitization procedure, new kinds of computerized wrongdoing have jumped up. Broad communications every dayreport episodes, for example, information spillage, individual information misrepresentation, adulteration of false archives and news.
One new innovation can furnish a leap forward in managing these criminal symptoms. This innovation - barricade, can possibly end up a standout amongst the most critical mechanical mainstays of the cutting edge world.
Desire
What was the standard method of task up to V-ID? Similarly, as it is currently hard to envision what the world resembled before the approach of the Internet, we trust that VID will turn into an all-around acknowledged and a broadly utilized component of the cutting edge computerized society.
V-ID will be utilized by any association that needs to shield its computerized documents from misrepresentation security. Think about how guaranteed SSL associations are right now utilized for sites.
At a later stage, V-ID can center around online recognizable proof and investigation of the two people and organizations.
Over the next 3 years, V-ID will become the market leader in file fraud protection, as SSL has become in the field of secure Internet connection.
After the private sale, funding will be allocated for a marketing campaign to promote the sale of tokens.
V-ID Token Utility offers a specific added value in identifying outstanding organizations, the preservation of digital fingerprint in the smart contract and the payment processor for verification.
The technical development of V-ID focuses on the wide application of Fail-safe for fraud prevention.
V-ID
Motives As society continues to digitalize, new types of digital crime are emerging. The media reported incidents such as data leaks, identity fraud, forgery and fake news on a daily basis.
Motives As society continues to digitalize, new types of digital crime are emerging. The media reported incidents such as data leaks, identity fraud, forgery and fake news on a daily basis.
One particular new technology could provide a breakthrough in the fight against these criminal side effects. This technology-blockchain, has the potential to become one of the most important technological pillars of the modern world.
Ambitions
What was the standard operating mode before V-ID? Just as it is difficult to imagine what the world was like before the advent of the Internet, we believe that VID will become a common and widely used element of modern digital society.
V-ID will be used by any organization that wants to protect their digital files from fraud in a secure way. Let's compare how certified SSL connections are currently used for websites.
V-ID will be used by any organization that wants to protect their digital files from fraud in a secure way. Let's compare how certified SSL connections are currently used for websites.
TOKENS
V-ID token administration is an ERC20 token that is utilized to distinguish the wallet address (for backers/checking parties) and is utilized as an installment for confirmation.
This stage can be utilized on the web (human interface) and will build the number of uses, SOAP, and BREAK API-interfaces, to frame the last secure extension to test the most widely recognized present-day programming (through web administrations and framework interfaces). Occasion Tokens are sold openly
TOKEN DISTRIBUTION
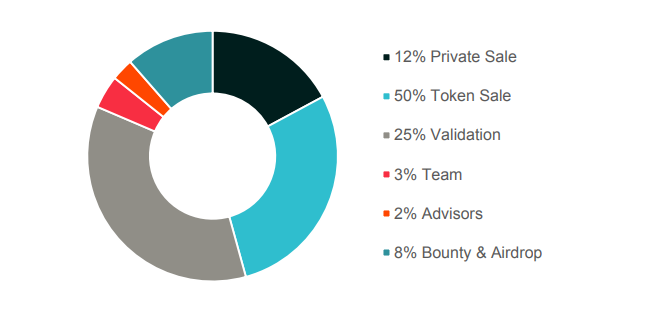
Pre Sales: September 15, 2018
General: 15 October 2018
End of Token Sale: December 15, 2018
The maximum number of VIDT tokens: 100,000,000
VIDT fee: $ 0.20
soft stamp: $ 1,000,000
Hard cap: $ 8,000,000
Thank you once again for taking the time to read this article, and thank you a million times for your support of V-ID.
For more information, visit the link below:
WEBSITE: https://token.v-id.org
Medium: https://medium.com/@pim_vee
Telegram: https://t.me/vidtoken
Facebook: https://www.facebook.com/ vidtoken
Twitter: https://twitter.com/v_id_blockchain
Github: https://github.com/v-id
Reddit: https://www.reddit.com/r/VIDT
author:Chubylaw



Tidak ada komentar:
Posting Komentar